Most Recent Cisco 300-910 Exam Dumps
Prepare for the Cisco Implementing DevOps Solutions and Practices using Cisco Platforms exam with our extensive collection of questions and answers. These practice Q&A are updated according to the latest syllabus, providing you with the tools needed to review and test your knowledge.
QA4Exam focus on the latest syllabus and exam objectives, our practice Q&A are designed to help you identify key topics and solidify your understanding. By focusing on the core curriculum, These Questions & Answers helps you cover all the essential topics, ensuring you're well-prepared for every section of the exam. Each question comes with a detailed explanation, offering valuable insights and helping you to learn from your mistakes. Whether you're looking to assess your progress or dive deeper into complex topics, our updated Q&A will provide the support you need to confidently approach the Cisco 300-910 exam and achieve success.
The questions for 300-910 were last updated on May 6, 2025.
- Viewing page 1 out of 26 pages.
- Viewing questions 1-5 out of 130 questions
Refer to the exhibit.
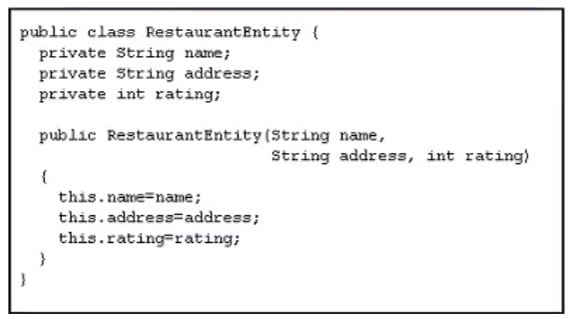
An application has been developed as a fileserver. To create this application as a fileserver. the class is used to store data in an SQL database.
Which two steps help minimize the risk of attack and compromise of the application? (Choose two.)
A new banking application is being developed as the main currency exchange resource for all the customers on a global scale. The application must comply with the security based on the deployed region. Therefore, the CI/CD pipeline must be created with the highest security possible.
Which approach accomplishes this goal?
A developer has created a deployment that should launch a pod to run their database service. The pod should launch with a metadata name of ''Cisco-DB," and the developer has added it to the "Cisco" namespace in their deployment.
Which Kubernetes command confirms that the service is running and usable?
The correct answer is B. kubectl -n Cisco get pods | grep 'Cisco-DB'. This command allows you to view the pods in the Cisco namespace and filter the list for the pod named 'Cisco-DB'. This will confirm that the pod is running and usable.
A security team is running vulnerability scans against a CI/CD pipeline. The reports show that RDBMS secrets were found hardcoded in Ansible scripts. The RDBMS resides in the internal network but is accessible from a jump server that resides in a public network.
If an attacker gains access to the scripts, what is the risk exposure?
The internal network is at risk of being compromised if an attacker gains access to the Ansible scripts, as the scripts contain hardcoded secrets for the RDBMS which is accessible from a jump server in a public network. This presents a risk as the secrets can be used to gain access to the RDBMS, and from there, the attacker could potentially gain access to the internal network. Additionally, the entire CI/CD-related infrastructure could be at risk if the attacker is able to gain access to the RDBMS, as they could potentially manipulate the data or scripts in order to cause disruption or damage.
What is as responsibility for teams running private cloud servers that is less of a concern when running in the public cloud?
The responsibility of credentials management is less of a concern when running in the public cloud. This is because the public cloud provider typically manages the credentials and handles authentication and authorization for the cloud services. In a private cloud environment, the organization must manage the credentials themselves, as well as authentication and authorization for the cloud services.
Unlock All Questions for Cisco 300-910 Exam
Full Exam Access, Actual Exam Questions, Validated Answers, Anytime Anywhere, No Download Limits, No Practice Limits
Get All 130 Questions & Answers