Most Recent CompTIA CS0-003 Exam Dumps
Prepare for the CompTIA Cybersecurity Analyst (CySA+) Exam exam with our extensive collection of questions and answers. These practice Q&A are updated according to the latest syllabus, providing you with the tools needed to review and test your knowledge.
QA4Exam focus on the latest syllabus and exam objectives, our practice Q&A are designed to help you identify key topics and solidify your understanding. By focusing on the core curriculum, These Questions & Answers helps you cover all the essential topics, ensuring you're well-prepared for every section of the exam. Each question comes with a detailed explanation, offering valuable insights and helping you to learn from your mistakes. Whether you're looking to assess your progress or dive deeper into complex topics, our updated Q&A will provide the support you need to confidently approach the CompTIA CS0-003 exam and achieve success.
The questions for CS0-003 were last updated on Jun 13, 2025.
- Viewing page 1 out of 86 pages.
- Viewing questions 1-5 out of 428 questions
During normal security monitoring activities, the following activity was observed:
cd C:\Users\Documents\HR\Employees
takeown/f .*
SUCCESS:
Which of the following best describes the potentially malicious activity observed?
The takeown command is used to take ownership of a file or folder that previously was denied access to the current user or group12. The activity observed indicates that someone has taken ownership of all files and folders under the C:\Users\Documents\HR\Employees directory, which may contain sensitive or confidential information. This could be a sign of unauthorized privileges, as the user or group may not have the legitimate right or need to access those files or folders. Taking ownership of files or folders could also enable the user or group to modify or delete them, which could affect the integrity or availability of the data.
A security analyst scans a host and generates the following output:
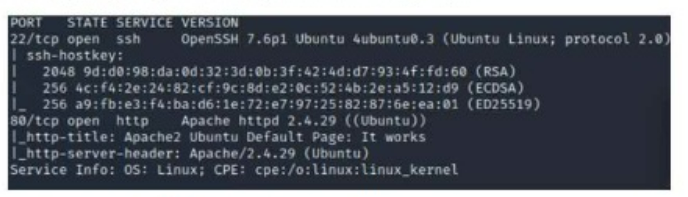
Which of the following best describes the output?
The output shows that port 80 is open and running an HTTP service, indicating that the host could potentially be vulnerable to web-based attacks.The other options are not relevant for this purpose: the host is responsive to the ICMP request, as shown by the ''Host is up'' message; the host is not running a mail server, as there is no SMTP or POP3 service detected; the host is not allowing unsecured FTP connections, as there is no FTP service detected.Reference:According to the CompTIA CySA+ Study Guide: Exam CS0-003, 3rd Edition123, one of the objectives for the exam is to ''use appropriate tools and methods to manage, prioritize and respond to attacks and vulnerabilities''. The book also covers the usage and syntax of nmap, a popular network scanning tool, in chapter 5.Specifically, it explains the meaning and function of each option in nmap, such as ''-sV'' for version detection2, page 195. Therefore, this is a reliable source to verify the answer to the question.
SIMULATION
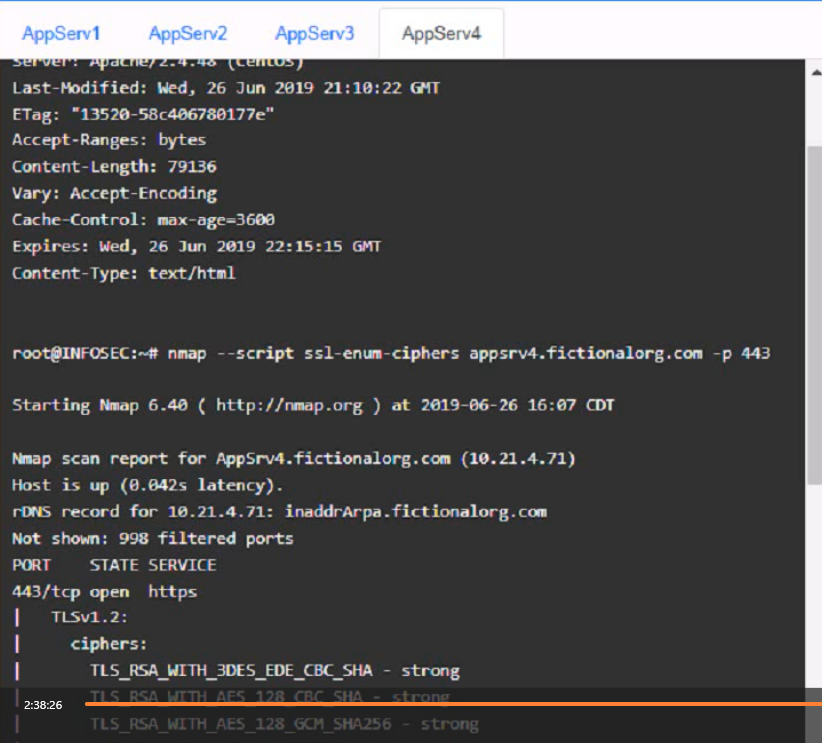
You are a cybersecurity analyst tasked with interpreting scan data from Company As servers You must verify the requirements are being met for all of the servers and recommend changes if you find they are not
The company's hardening guidelines indicate the following
* TLS 1 2 is the only version of TLS
running.
* Apache 2.4.18 or greater should be used.
* Only default ports should be used.
INSTRUCTIONS
using the supplied dat
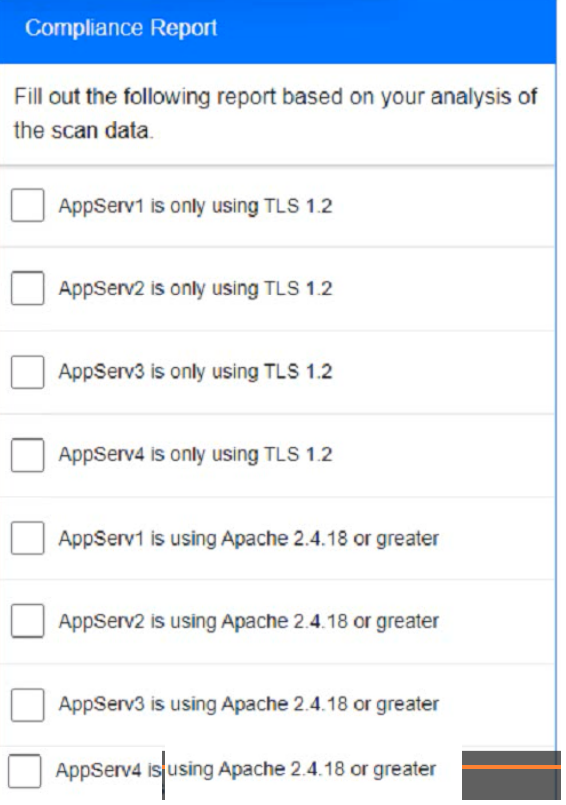
a. record the status of compliance With the company's guidelines for each server.
The question contains two parts: make sure you complete Part 1 and Part 2. Make recommendations for Issues based ONLY on the hardening guidelines provided.
Part 1:
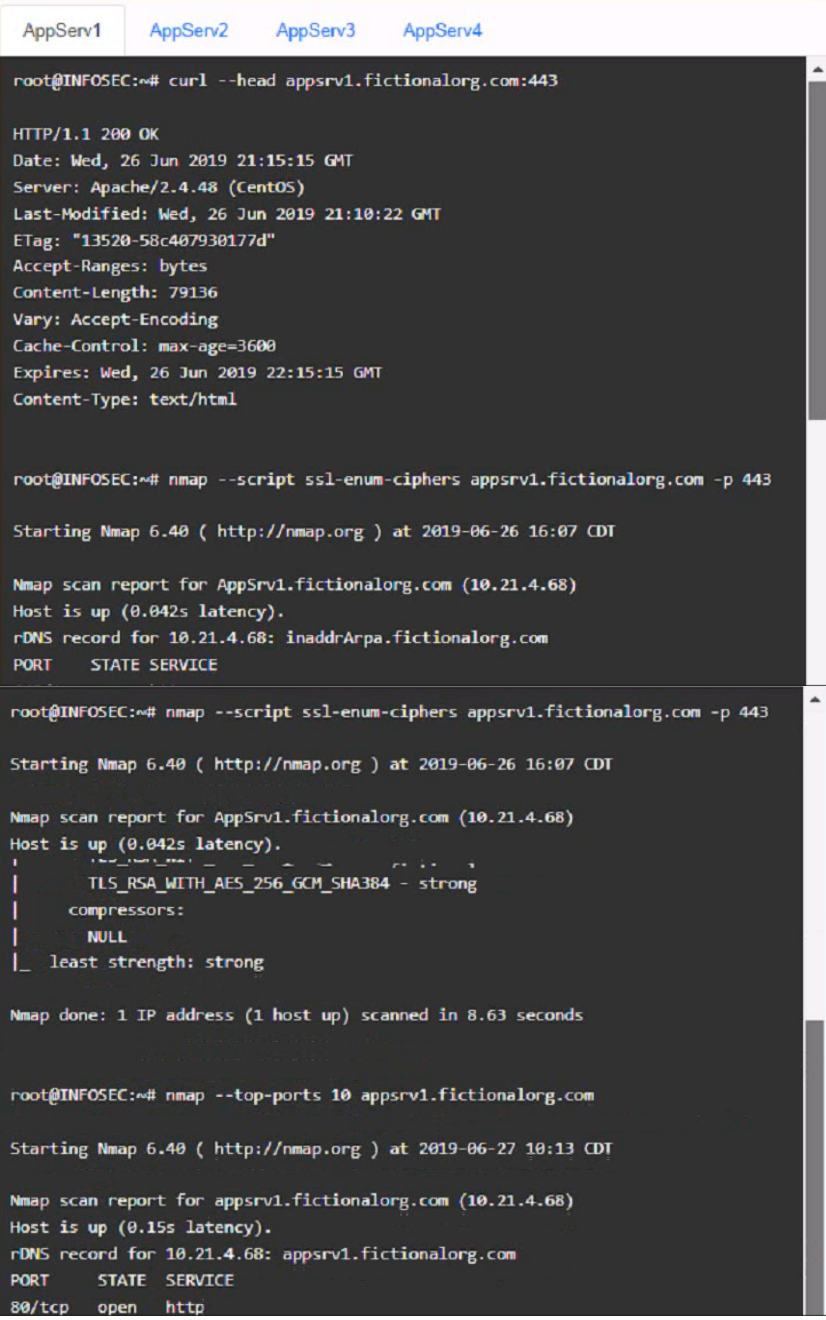
AppServ1:
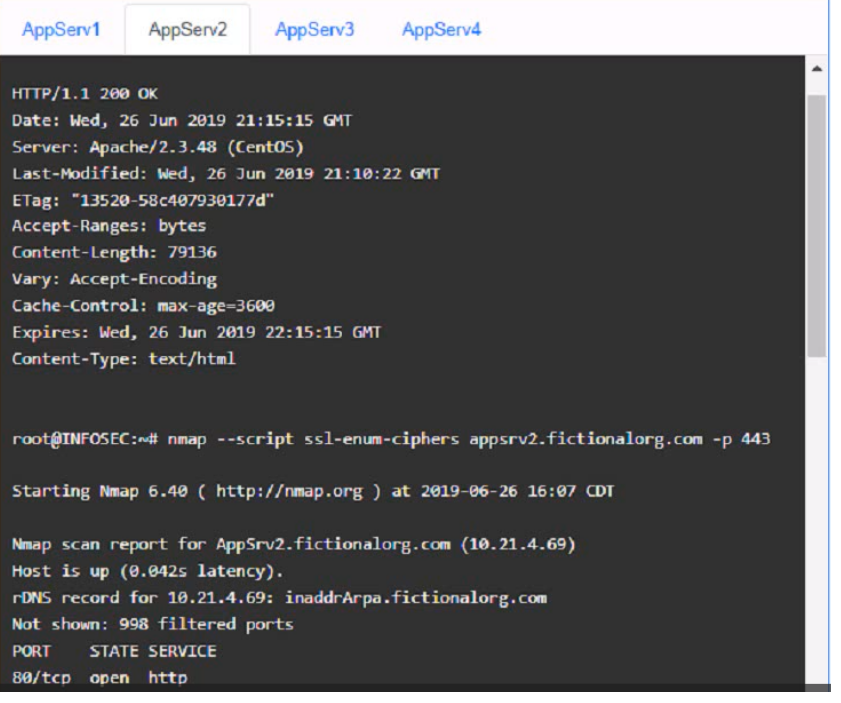
AppServ2:
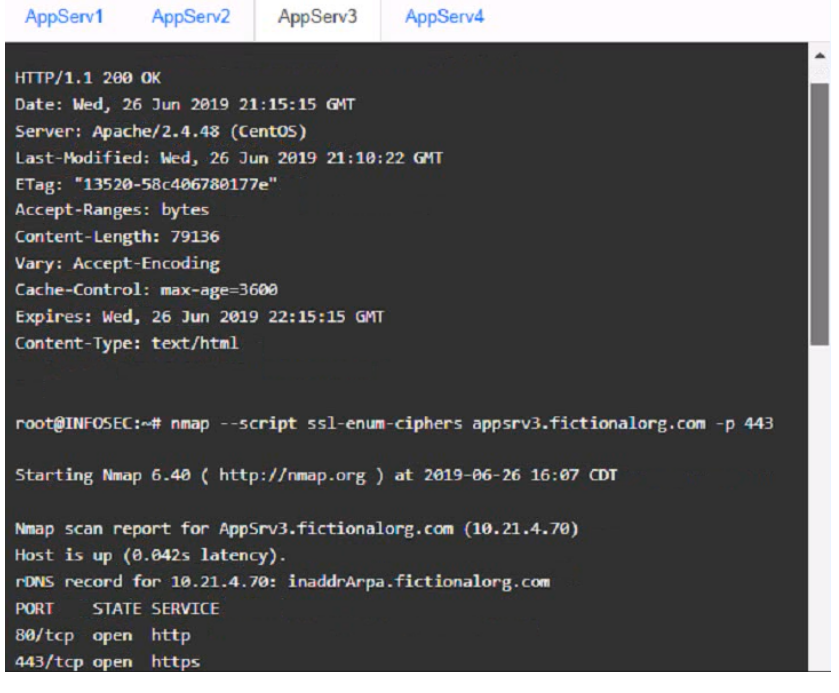
AppServ3:
AppServ4:
Part 2:
Part 1:

Part 2:
Based on the compliance report, I recommend the following changes for each server:
AppServ1: No changes are needed for this server.
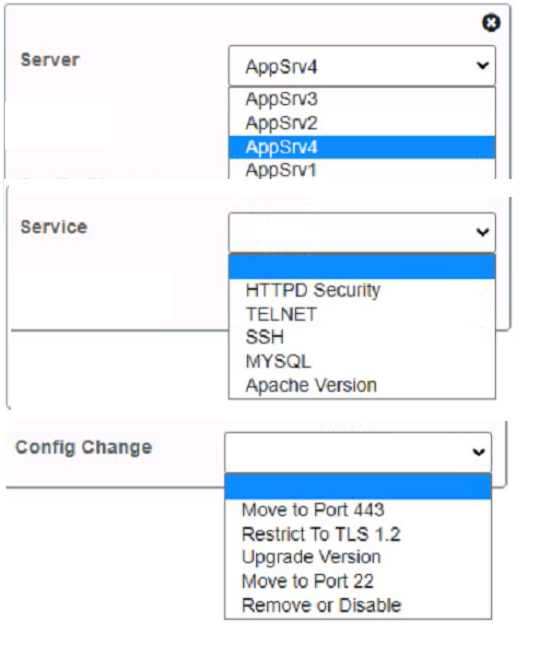
AppServ2: Disable or upgrade TLS 1.0 and TLS 1.1 to TLS 1.2 on this server to ensure secure encryption and communication between clients and the server. Update Apache from version 2.4.17 to version 2.4.18 or greater on this server to fix any potential vulnerabilities or bugs.
AppServ3: Downgrade Apache from version 2.4.19 to version 2.4.18 or lower on this server to ensure compatibility and stability with the company's applications and policies. Change the port number from 8080 to either port 80 (for HTTP) or port 443 (for HTTPS) on this server to follow the default port convention and avoid any confusion or conflicts with other services.
AppServ4: Update Apache from version 2.4.16 to version 2.4.18 or greater on this server to fix any potential vulnerabilities or bugs. Change the port number from 8443 to either port 80 (for HTTP) or port 443 (for HTTPS) on this server to follow the default port convention and avoid any confusion or conflicts with other services.
Which of the following is a circumstance in which a security operations manager would most likely consider using automation?
Automating the generation of NIDS (Network Intrusion Detection System) rules based on Structured Threat Information eXpression (STIX) messages is a practical use of automation in security operations.
Option B (Privileged access requests) should involve human oversight due to the high risk of unauthorized access.
Option C (PKI identity verification) requires manual document verification and human approval.
Option D (Malware analysis) often requires sandboxing and behavioral analysis, which benefit from human expertise.
Thus, A is the correct answer, as automating threat intelligence ingestion and rule creation enhances efficiency in intrusion detection.
During an extended holiday break, a company suffered a security incident. This information was properly relayed to appropriate personnel in a timely manner and the server was up to date and configured with appropriate auditing and logging. The Chief Information Security Officer wants to find out precisely what happened. Which of the following actions should the analyst take first?
The first action that the analyst should take in this case is to clone the virtual server for forensic analysis. Cloning the virtual server involves creating an exact copy or image of the server's data and state at a specific point in time. Cloning the virtual server can help preserve and protect any evidence or information related to the security incident, as well as prevent any tampering, contamination, or destruction of evidence. Cloning the virtual server can also allow the analyst to safely analyze and investigate the incident without affecting the original server or its operations.
Unlock All Questions for CompTIA CS0-003 Exam
Full Exam Access, Actual Exam Questions, Validated Answers, Anytime Anywhere, No Download Limits, No Practice Limits
Get All 428 Questions & Answers