Most Recent Juniper JN0-637 Exam Dumps
Prepare for the Juniper Security, Professional exam with our extensive collection of questions and answers. These practice Q&A are updated according to the latest syllabus, providing you with the tools needed to review and test your knowledge.
QA4Exam focus on the latest syllabus and exam objectives, our practice Q&A are designed to help you identify key topics and solidify your understanding. By focusing on the core curriculum, These Questions & Answers helps you cover all the essential topics, ensuring you're well-prepared for every section of the exam. Each question comes with a detailed explanation, offering valuable insights and helping you to learn from your mistakes. Whether you're looking to assess your progress or dive deeper into complex topics, our updated Q&A will provide the support you need to confidently approach the Juniper JN0-637 exam and achieve success.
The questions for JN0-637 were last updated on May 1, 2025.
- Viewing page 1 out of 23 pages.
- Viewing questions 1-5 out of 115 questions
You have deployed an SRX Series device at your network edge to secure Internet-bound sessions for your local hosts using source NAT. You want to ensure that your users are able to interact with applications on the Internet that require more than one TCP session for the same application session.
Which two features would satisfy this requirement? (Choose two.)
Address persistence ensures that the same NAT IP address is used for all sessions originating from a single source IP. Persistent NAT maintains connections for applications needing multiple sessions, like VoIP. Additional details are available in Juniper NAT Documentation.
For applications that require multiple TCP sessions for the same application session (such as VoIP or certain online games), the SRX device needs to handle NAT properly to maintain session continuity. Here's what helps:
Address Persistence (Answer A): Address persistence ensures that multiple sessions initiated by the same internal host are mapped to the same external IP address. This is crucial for applications that use multiple TCP sessions to maintain a stateful connection with the external server.
Command Example:
bash
set security nat source persistent-nat address-persistence
Persistent NAT (Answer C): This feature allows the external server to initiate new connections to the internal client using the same NAT translation. It's essential for applications that require consistent NAT mappings across multiple sessions.
Command Example:
bash
set security nat source persistent-nat permit target-host-port
These features ensure that applications with multiple TCP sessions work seamlessly across NAT.
Exhibit:
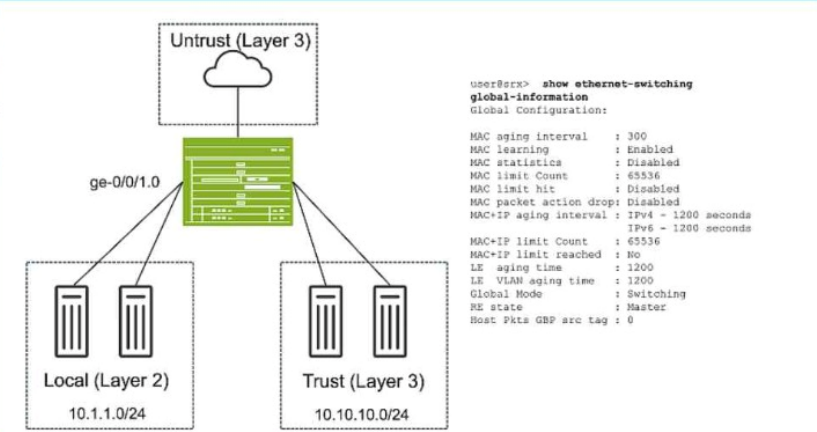
Referring to the exhibit, which two statements are true? (Choose two.)
You are deploying threat remediation to endpoints connected through third-party devices.
In this scenario, which three statements are correct? (Choose three.)
For threat remediation in a third-party network, the RADIUS protocol is necessary to communicate with the RADIUS server for details about infected hosts. CoA enables security measures to be enforced based on endpoint information provided by the RADIUS server. Details on this setup can be found in Juniper RADIUS and AAA Documentation.
When deploying threat remediation to endpoints connected through third-party devices, such as switches, the following conditions must be met for proper integration and functioning:
Explanation of Answer A (Support for AAA/RADIUS and Dynamic Authorization Extensions):
Third-party switches must support AAA (Authentication, Authorization, and Accounting) and RADIUS with Dynamic Authorization Extensions. These extensions allow dynamic updates to be made to a session's authorization parameters, which are essential for enforcing access control based on threat detection.
Explanation of Answer B (Connector Gathers MAC Information via API):
The connector uses an API to gather MAC address information from the RADIUS server. This MAC address data is necessary to identify and take action on infected hosts or endpoints.
Explanation of Answer D (Connector Initiates CoA):
The connector queries the RADIUS server for infected host details and triggers a Change of Authorization (CoA) for the infected host. The CoA allows the connector to dynamically alter the host's access permissions or isolate the infected host based on its threat status.
Juniper Security Reference:
Threat Remediation via RADIUS: Dynamic remediation actions, such as CoA, can be taken based on information received from the RADIUS server regarding infected hosts. Reference: Juniper RADIUS and CoA Documentation.
You are enabling advanced policy-based routing. You have configured a static route that has a next hop from the inet.0 routing table. Unfortunately, this static route is not active in your routing instance.
In this scenario, which solution is needed to use this next hop?
To enable advanced policy-based routing in Junos OS and activate a static route with a next-hop address in the inet.0 table within your routing instance, you should utilize RIB groups. RIB groups allow you to import routes from one routing table to another. In this scenario, the static route within the routing instance needs access to the inet.0 routes, which is facilitated by configuring a RIB group. Juniper's documentation outlines RIB groups as a necessary component for handling instances where routes need to be shared across routing tables, thereby ensuring seamless traffic flow through specified routes. For more details, refer to the Juniper Networks Documentation on RIB Groups.
In Junos OS for SRX Series devices, when enabling advanced policy-based routing and configuring a static route with a next-hop from the inet.0 routing table, the issue arises because the static route is not being used in the routing instance. This is a common scenario when the next-hop belongs to a different routing table or instance, and the routing instance is not aware of that next-hop.
To resolve this, RIB (Routing Information Base) groups are used. RIB groups allow routes from one routing table (RIB) to be shared or imported into another routing table. This means that the routing instance can import the necessary routes from inet.0 and make them available for the routing instance where the policy-based routing is applied.
Detailed Steps:
Configure the Static Route: First, configure the static route pointing to the next-hop in inet.0. Here's an example:
bash
set routing-options static route 10.1.1.0/24 next-hop 192.168.1.1
This static route will be placed in the inet.0 routing table by default.
Create and Apply a RIB Group: To import routes from inet.0 into the routing instance, create a RIB group configuration. This will allow the static route from inet.0 to be visible within the routing instance.
Example configuration for the RIB group:
bash
set routing-options rib-groups RIB-GROUP import-rib inet.0
set routing-options rib-groups RIB-GROUP import-rib <routing-instance-name>.inet.0
This configuration ensures that routes from inet.0 are imported into the specified routing instance.
Apply the RIB Group to the Routing Instance: Once the RIB group is configured, apply it to the appropriate routing instance:
bash
set routing-instances <routing-instance-name> routing-options rib-group RIB-GROUP
Verify Configuration: Use the following command to verify that the static route has been imported into the routing instance:
bash
show route table <routing-instance-name>.inet.0
The output should now display the static route imported from inet.0.
Juniper Security Reference:
RIB Groups Overview: Juniper's documentation provides detailed information on how RIB groups function and how to use them to share routes between different routing tables. This is essential for scenarios involving policy-based routing where routes from one instance (like inet.0) need to be available in another instance. Reference: Juniper Networks Documentation on RIB Groups.
By using RIB groups, you ensure that the static route from inet.0 is available in the appropriate routing instance for policy-based routing to function correctly. This avoids the need for other methods like filter-based forwarding or transparent mode, which do not address the specific issue of static route visibility across routing instances.
You are configuring advanced policy-based routing. You have created a static route with next
hop of an interface in your inet.0 routing table
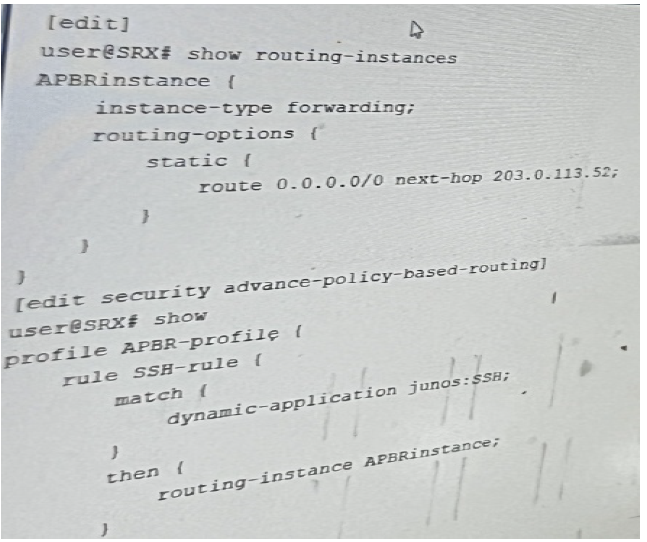

Referring to the exhibit, what should be changed to solve this issue?
Unlock All Questions for Juniper JN0-637 Exam
Full Exam Access, Actual Exam Questions, Validated Answers, Anytime Anywhere, No Download Limits, No Practice Limits
Get All 115 Questions & Answers