Most Recent Netskope NSK101 Exam Dumps
Prepare for the Netskope Certified Cloud Security Administrator Exam exam with our extensive collection of questions and answers. These practice Q&A are updated according to the latest syllabus, providing you with the tools needed to review and test your knowledge.
QA4Exam focus on the latest syllabus and exam objectives, our practice Q&A are designed to help you identify key topics and solidify your understanding. By focusing on the core curriculum, These Questions & Answers helps you cover all the essential topics, ensuring you're well-prepared for every section of the exam. Each question comes with a detailed explanation, offering valuable insights and helping you to learn from your mistakes. Whether you're looking to assess your progress or dive deeper into complex topics, our updated Q&A will provide the support you need to confidently approach the Netskope NSK101 exam and achieve success.
The questions for NSK101 were last updated on May 4, 2025.
- Viewing page 1 out of 26 pages.
- Viewing questions 1-5 out of 129 questions
You need to locate events for specific activities such as "edit" or "login successful" in a cloud application.
In which SkopeIT Events & Alerts page would this information be found?
The Application Events page in the SkopeIT Events & Alerts section is where you can find logs and events related to specific activities within cloud applications, such as 'edit' or 'login successful'. This section provides a detailed audit trail of user activities and application usage, which is essential for monitoring, security, and compliance purposes.
This answer is validated by the event categorization provided in the Netskope documentation, where application-specific events are logged under the Application Events section for easier tracking and analysis.
========
REST API v2 Overview - Netskope Knowledge Portal
Using the REST API v2 UCI Impact Endpoints - Netskope Knowledge Portal
Postman Collection for Netskope API
You want to block access to sites that use self-signed certificates. Which statement is true in this scenario?
Click the Exhibit button.
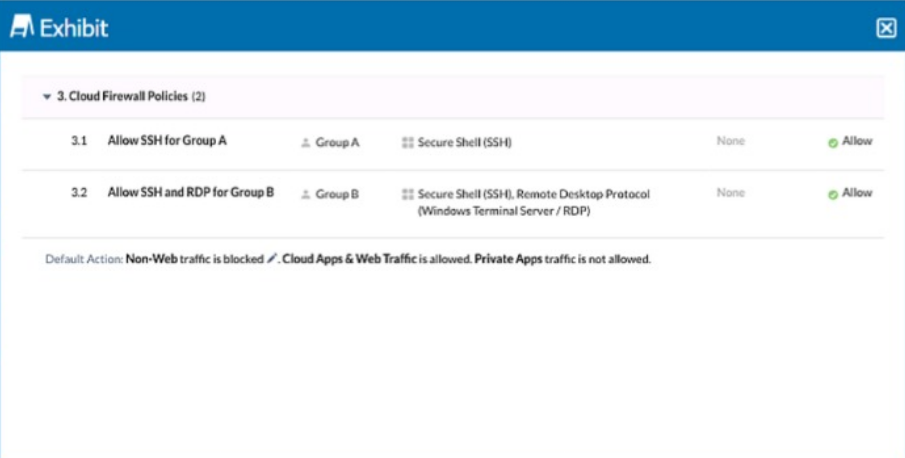
You configured a set of Cloud Firewall policies as shown in the exhibit and changed your Steering Configuration to All Traffic for Group A and Group B. Users in Group A report that they are unable to access a third-party server using TCP port 3389. Referring to the exhibit, which action correctly describes how you would allow these connections without allowing unnecessary access?
The exhibit shows that Group A is allowed only SSH traffic, while Group B is allowed both SSH and RDP traffic. Since users in Group A need access to a third-party server using TCP port 3389 (RDP), you need to create a specific policy to allow this traffic without granting unnecessary access.
Creating an Allow policy using a custom application that includes the destination IP and TCP port 3389 will precisely target the required traffic and ensure that only the necessary connections are permitted. This method avoids broader policy changes that could introduce unnecessary access.
Netskope documentation on creating and managing Cloud Firewall policies.
Best practices for configuring application-specific policies to control network traffic effectively.
What are two fundamental differences between the inline and API implementation of the Netskope platform? (Choose two.)
The inline and API implementation of the Netskope platform are two different ways of connecting cloud applications to Netskope for inspection and policy enforcement. Two fundamental differences between them are: The API implementation can only be used with sanctioned applications, which are applications that are approved and authorized by the organization for business use. The API implementation relies on using out-of-band API connections to access data and events from these applications and apply near real-time policies. The inline implementation can effectively block a transaction in both sanctioned and unsanctioned applications, which are applications that are not approved or authorized by the organization for business use. The inline implementation relies on using in-band proxy or reverse-proxy connections to intercept traffic to and from these applications and apply real-time policies. The API implementation can be used with both sanctioned and unsanctioned applications and the inline implementation can only effectively block a transaction in sanctioned applications are not true statements, as they contradict the actual capabilities and limitations of each implementation method.Reference:[Netskope SaaS API-enabled Protection], [Netskope Inline CASB].
Unlock All Questions for Netskope NSK101 Exam
Full Exam Access, Actual Exam Questions, Validated Answers, Anytime Anywhere, No Download Limits, No Practice Limits
Get All 129 Questions & Answers